RO7: SecureCEdit: Secure Collaborative and Concurrent Editing
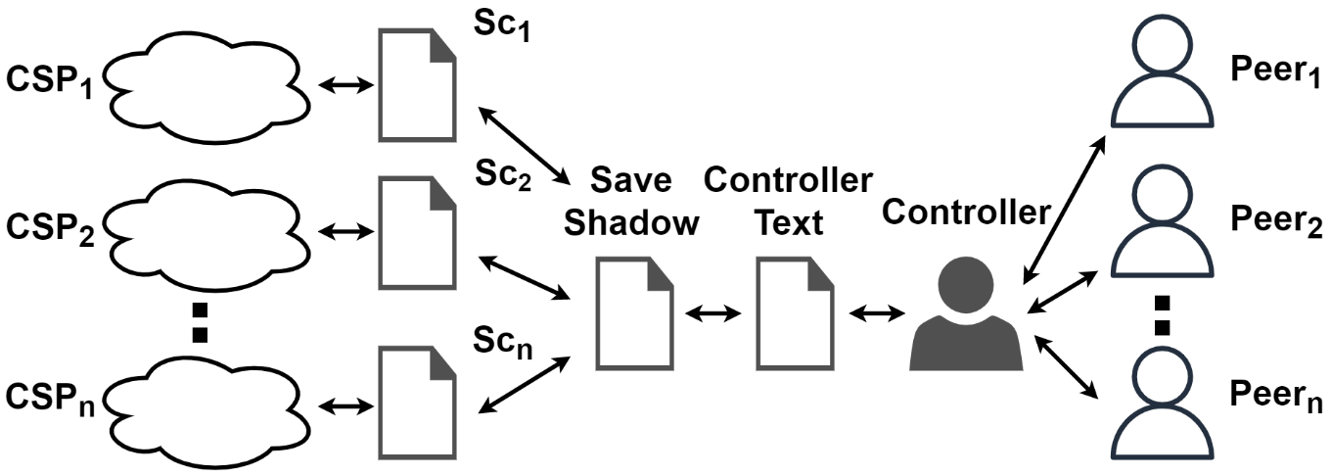
We assert that in online editing environments, such as, Google Docs and Office 365, user data should never be exposed to the cloud in an unencrypted format. Prior research on secure collaborative editing has exhibited several limitations and lacks practicality. Therefore, in this study, we introduced a secure framework for online editing, termed SecureC2Edit. This framework operates on a structured peer-to-peer architecture, employing hybrid differential synchronization. It facilitates collaborative and simultaneous document access while ensuring data security and privacy through encryption before cloud storage.
Publications:
S. Arora and P. K. Atrey. SecureC2Edit: A framework for secure collaborative and concurrent
document editing. IEEE Transactions on Dependable and Secure Computing (TDSC) (2023)
(Early access available).[pdf][bibtex]
S. Arora and P. K. Atrey. Secure collaborative editing using secret sharing. IEEE Workshop
on Information Forensics and Security (WIFS’21), Montpellier, France, December 2021.[pdf][bibtex]
S. Arora, G. Varshney, P. K. Atrey, and M. Mishra. SecureCEdit: An approach for secure
cloud-based document editing. The 2nd IEEE Workshop on Security and Privacy in the Cloud
(SPC 2016) in conjunction with IEEE Conf. on Communications and Network Security (CNS
2016), Philadelphia, PA, USA, October 2016.[pdf][bibtex]
RO6: SecureCMail: Securing Emails from Service Providers
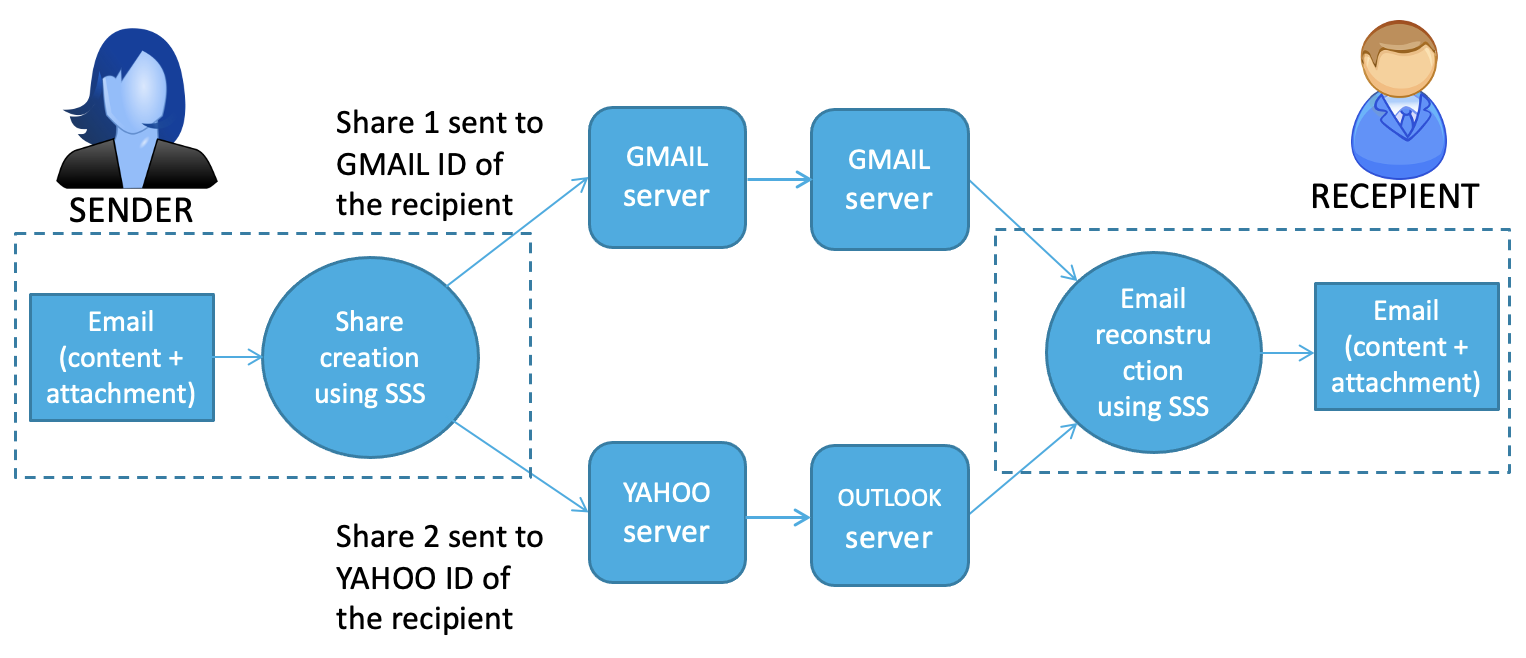
Frequently, we transmit sensitive information like passport details, credit card data, and social security numbers via email without considering the security of email services. Although current network security measures offer reasonable protection against external threats and eavesdroppers, they do not assure that email service providers (ESPs) cannot access our email content, which might contain highly sensitive information. One potential approach to safeguard email data from ESP access involves using Pretty Good Privacy (PGP), yet PGP comes with several limitations, including issues with key storage and reliance on third-party services, resulting in practical difficulties when used. We introduced a method, called SecureCMail, designed to enhance email security against ESPs. This approach employs cryptographic secret sharing techniques to encrypt the metadata, body, and attachments of emails before transmission. Within this solution, both the email sender and recipient must possess at least two email accounts hosted on existing ESPs, a practice that has become increasingly common.
Publications:
P. Singh, S. Arora, K. Williamson, and P. K. Atrey. S3Email: A method for securing emails
from service providers. The 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC’2017), Banff, Canada, October 2017. [pdf][bibtex]
Q5: SecureCMerge and SecureCSearch: Secure PDF Merging and Searching over Untrusted Servers

The act of merging multiple PDF files is a routine task frequently conducted by users, often utilizing freely accessible online tools like pdfmerge or cloud-based services such as cloudconvert. However, the reliability of these free online servers cannot always be guaranteed and may pose potential risks to the confidentiality of the PDF files. In our study, we introduced a method named SecureCMerge. This approach enables the secure merging of PDF files using free online merge sites. Furthermore, the extended SecureCSearch method facilitates efficient keyword search operations on encrypted PDF files over the cloud.
Publications:
N. Sharma, P Singh, and P. K. Atrey. SecureCMerge: Secure PDF merging over untrusted
servers. The 1st IEEE International Conference on Multimedia Information Processing and
Retrieval (MIPR’18), Miami, FL, USA, April 2018. [pdf][bibtex]
M. Shah, M. Mohanty, and P. K. Atrey. SecureCSearch: Secure searching in PDF over untrusted cloud servers. The 2nd IEEE International Conference on Multimedia Information Processing and Retrieval (MIPR’19), San Jose, CA, USA, March 2019. [pdf][bibtex]
RO4: SecureCSocial: Secure Cloud-based Social Network
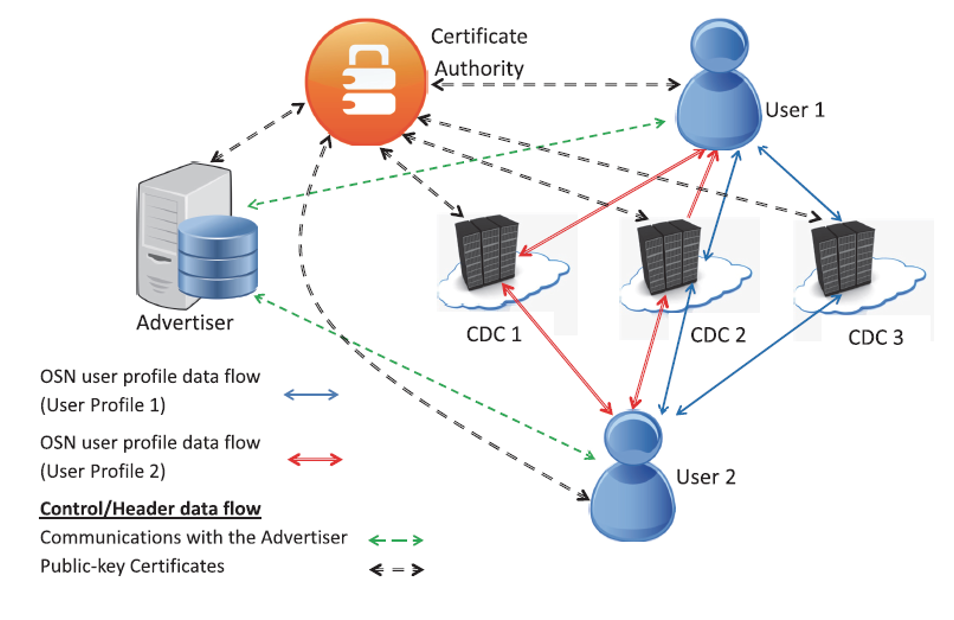
The use of social networks has grown exponentially in recent years, and these social networks continue to have an ever-increasing impact on human lives. There are many concerns regarding the privacy of users in these environments, such as how trustworthy the social network operators are, in addition to the external adversaries. In this work, we proposed a new architecture for online social networking, based on distributed cloud-based datacenters and using secret sharing as the method of encrypting user profile data, for enhanced privacy and availability. The proposed architecture is analyzed for its security and performance along with experimental analysis.
Publications:
P. K. Atrey and K. Senevirathna. SecureCSocial: Secure cloud-based social network. World Scientific Series in Digital Forensics and Cybersecurity: Volume 1, August 2019. [pdf][bibtex]
K. Senevirathna and P. K. Atrey. A secure and privacy-aware cloud-based architecture for online social networks. The 7th Multi-Disciplinary International Workshop on Artificial Intelligence (MIWAI'2013), December 2013, Krabi, Thailand. [pdf][bibtex]
RO3: SecureCEnhance: Enhancement of Image/Video/Audio in Encrypted Domain
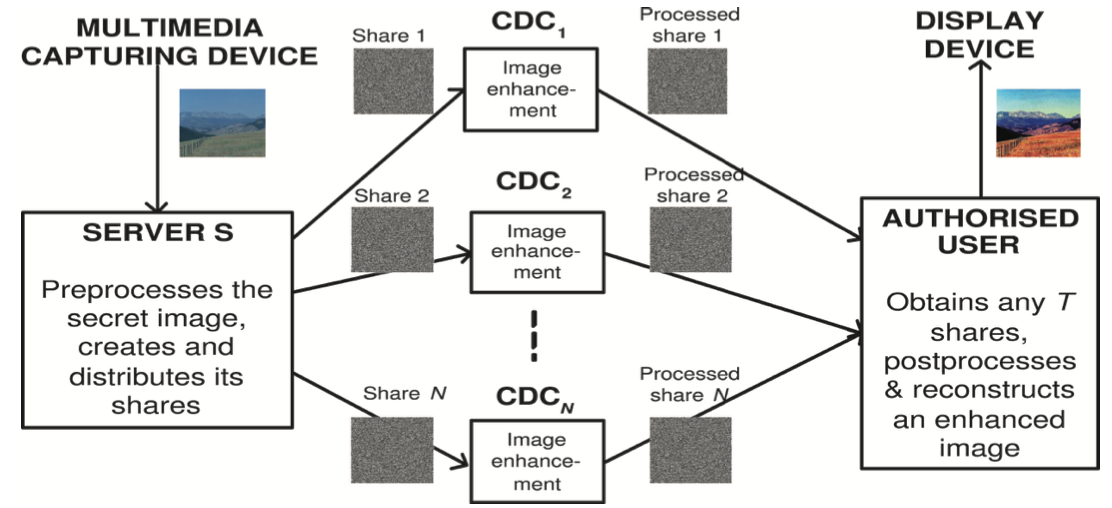
Improving quality of multimedia data is paramount in many advanced tasks such as object detection and tracking and scene understanding. In this research, we used the SecureCSuite framework to enhance the quality of encrypted image, and audio data over cloud.
Demos:
- Secure Image Constrast Enhancement: [Demo Video].
- Secure Image Dehazing: [Demo Video].
Publications:
A. Yakubu, N. Maddage, and P. K. Atrey. Securing speech noise eeduction in outsourced environment. ACM Transactions on Multimedia Computing, Communication and Applications,
Vol. 13, No. 4, Article 51 (2017).[pdf][bibtex]
A. Lathey and P. K. Atrey. Image enhancement in encrypted domain over cloud. ACM Trans.
on Multimedia Computing, Communications and Applications, Vol. 11, No. 3, Article 38
(2015). [pdf][bibtex]
A. Lathey, P. K. Atrey, and N. Joshi. Homomorphic low pass filtering on encrypted multimedia
over cloud. IEEE Int. Conf. on Semantic Computing (ICSC’13), Sep. 2013, Irvine, CA, USA. [pdf][bibtex]
A. Yakubu, N. C. Maddage, and P. K. Atrey. Audio secret management scheme using Shamir’s
secret sharing. The 21st Int. Conf. on Multimedia Modeling (MMM’15), Jan. 2015, Sydney,
Australia. [pdf][bibtex]
A. Yakubu, N. C. Maddage, and P. K. Atrey. Secure audio reverberation over cloud. The 10th
Annual Symp. on Information Assurance in conjunction with The 18th New York State Cyber
Security Conf. (ASIA’15), Albany, NY, USA, Jun. 2015. [pdf][bibtex]
A. Yakubu, N. C. Maddage, and P. K. Atrey. Encrypted domain cloud-based speech noise
reduction with comb filter. The first IEEE Int. Workshop on ”Privacy Issues in Multimedia”
(PIM’16) in conjunction with IEEE Int. Conf. on Multimedia and Expo (ICME’16), Seattle,
WA, USA, Jul. 2016. [pdf][bibtex]
RO2: SecureCScale: Scaling and Cropping of Image/Video in Encrypted Form
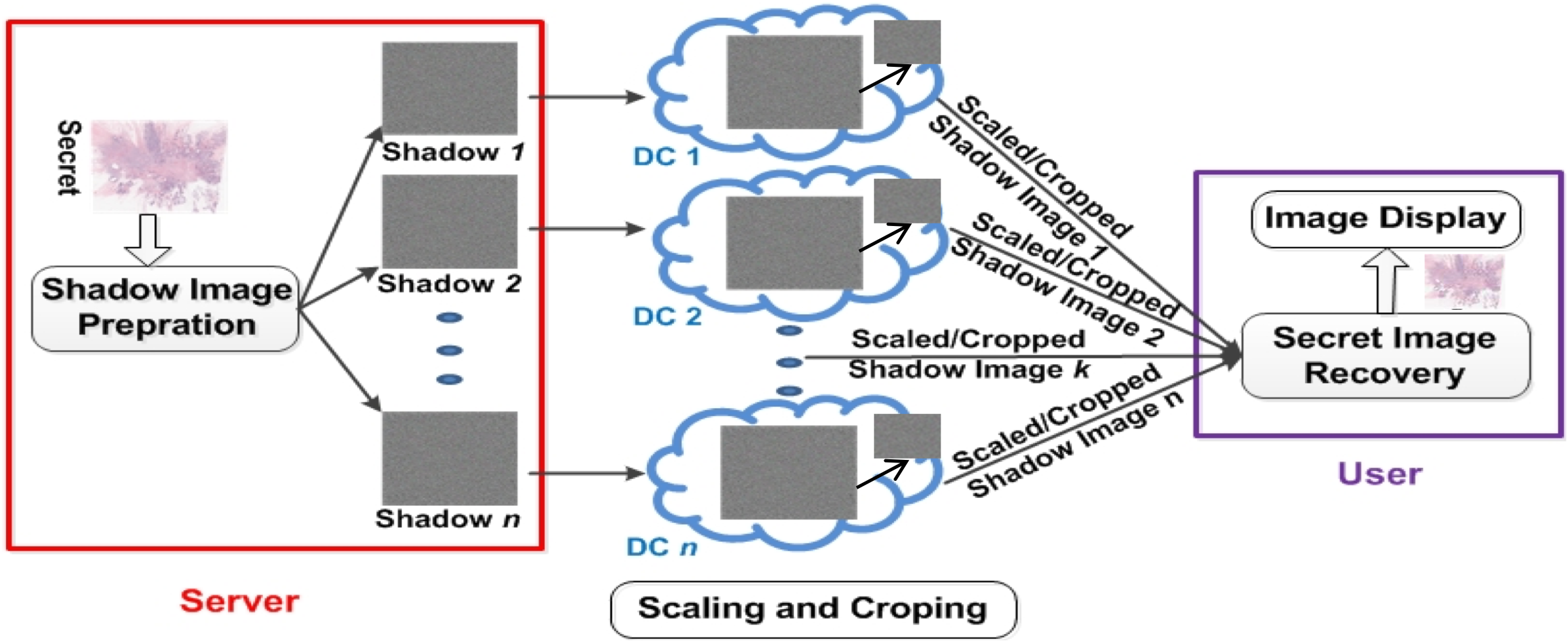
Resizing and cropping images or videos are prevalent functions utilized across various applications, including social media platforms and computational photography. We expanded the functionalities of the SecureCSuite framework to accommodate scaling and cropping operations on encrypted image and video data through cloud-based processing.
Demos:
- Secure Video Scaling and Cropping: Demo Video.
Publications:
M. Mohanty, W.-T. Ooi, and P. K. Atrey. Scale me, crop me, know me not: Supporting scaling
and cropping in secret image sharing. IEEE Int. Conf. on Multimedia and Expo (ICME’13),
Jul. 2013, San Jose, CA, USA.[pdf][bibtex]
K. Kansal, M. Mohanty, and P. K. Atrey. Scaling and cropping of wavelet-based compressed
images in hidden domain. The 21st Int. Conf. on Multimedia Modeling (MMM’15), Jan.
2015, Sydney, Australia.[pdf][bibtex]
O.-A. Kristensen, M. Mohanty, and P. K. Atrey. Don’t See Me, Just Edit Me: Towards Secure
Cloud-based Video Editing. The 11th Annual Symp. on Information Assurance in conjunction
with The 19th New York State Cyber Security Conf. (ASIA’16), pp 74-78, Albany, NY, USA,
Jun. 2016. [pdf][bibtex]
RO1: SecureCVolume: Secure Cloud-based Volume Ray-casting
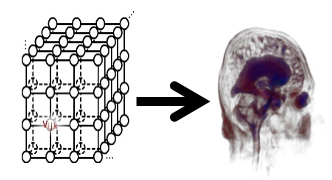
Outsourcing the tasks of medical data visualization to cloud centers presents new security challenges. In this work, we proposed a framework for cloud-based remote medical data visualization that protects the data at the cloud centers. To achieve this, we integrated the cryptographic secret sharing with pre-classification volume ray-casting and propose a secure volume ray-casting pipeline that hides the color-coded information of the secret medical data during rendering at the data centers.
Publications:
M. Mohanty, W.T. Ooi, and P. K. Atrey. Secret sharing approach for securing cloud-based
pre-classification volume ray-casting. Springer Int. J. Multimedia Tools and Applications. Vol.
75, Issue 11, pp 6207–6235 (2016). [pdf][bibtex]
M. Mohanty, P. K. Atrey, and W.-T. Ooi. Secure cloud-based medical data visualization. The
ACM Int. Conf. on Multimedia (ACMMM’12), pp 1105-1108, Oct. 29-Nov. 2, 2012, Nara,
Japan. [pdf][bibtex]
 Pradeep Atrey's Research on
Pradeep Atrey's Research on